Ronald Deibert
2014-02-12 17:01:28 UTC
Hello LibTech
On behalf of the Citizen Lab, I am pleased to announce a new publication, details for which are below. This report is the first in a series that focus
on the global proliferation and use of Hacking Team's RCS spyware, sold exclusively to governments. More posts will follow in the next week.
The report is authored by Bill Marczak, Claudio Guarnieri, Morgan Marquis-Boire, and John Scott-Railton. I'd like to draw attention to the innovative
mixed scanning methods developed in this post, around which a new field of research is emerging which I believe is going to be critical to the
type of distributed civil controls on the global spyware market.
Regards
Ron
https://citizenlab.org/2014/02/hackingteam-targeting-ethiopian-journalists/
Hacking Team and the Targeting of Ethiopian Journalists
February 12, 2014
Tagged: Ethiopia, Hacking Team
Categories: News and Announcements, Reports and Briefings, Research News
Authors: Bill Marczak, Claudio Guarnieri, Morgan Marquis-Boire, and John Scott-Railton.
This post is the first in a series of posts that focus on the global proliferation and use of Hacking Team?s RCS spyware, sold exclusively to governments.
Summary
Ethiopian Satellite Television Service1 (ESAT) is an independent satellite television, radio, and online news media outlet run by members of the Ethiopian diaspora. The service has operations in Alexandria, Virginia, as well as several other countries.2 ESAT?s broadcasts are frequently critical of the Ethiopian Government. Available in Ethiopia and around the world, ESAT has been subjected to jamming from within Ethiopia several times in the past few years.3 A recent documentary shown on Ethiopian state media warned opposition parties against participating in ESAT programming.4
In the space of two hours on 20 December 2013, an attacker made three separate attempts to target two ESAT employees with sophisticated computer spyware, designed to steal files and passwords, and intercept Skype calls and instant messages. The spyware communicated with an IP address belonging to Ariave Satcom, a satellite provider that services Africa, Europe, and Asia.5 In each case, the spyware appeared to be Remote Control System (RCS), sold exclusively to governments by Milan-based Hacking Team.6
Hacking Team states that they do not sell RCS to ?repressive regimes?,7 and that RCS is not sold through ?independent agents?.8 Hacking Team also says that all sales are reviewed by a board that includes outside engineers and lawyers. The board has veto power over any sale.9 Before authorizing a sale, the company states that it considers ?credible government or non-government reports reflecting that a potential customer could use surveillance technologies to facilitate human rights abuses,? as well as ?due process requirements? for surveillance.10
The Committee to Protect Journalists (CPJ) reports that Ethiopia jails more journalists than any other African country besides Eritrea, and says that the Ethiopian government has shut down more than 75 media outlets since 1993.11 CPJ statistics also show that 79 journalists have been forced to flee Ethiopia due to threats and intimidation over the past decade, more than any other country in the world.12 A 2013 Human Rights Watch (HRW) report detailed ongoing torture at Ethiopia?s Maekelawi detention center, the first stop for arrested journalists and protests organizers. Former detainees described how they were: ?repeatedly slapped, kicked, punched, and beaten,? and hung from the ceiling by their wrists. Information extracted in confession has been used to obtain conviction at trial, and to compel former detainees to work with the government.13 HRW also indicated abuses committed by the army, including the use of torture and rape to compel information from villagers near the site of an attack on a farm.14 HRW noted ?insufficient respect for ? due process? in Ethiopia.15
Background
Hacking Team and Remote Control System (RCS)
Hacking Team, also known as HT S.r.l., is a Milan-based purveyor of ?offensive technology? to governments around the world. One of their products, known as Remote Control System (RCS), is a trojan that is sold exclusively to intelligence and law enforcement agencies worldwide. Hacking Team?s website describes the product as ?the solution? to monitor targets that are increasingly using encryption, or those located outside the borders of the government that wants to monitor them.16
Description of RCS in a 2011 official brochure.17
RCS infects a target?s computer or mobile phone to intercept data before it is encrypted for transmission, and can also intercept data that is never transmitted. For example, it can copy files from a computer?s hard disk, and can also record Skype calls, e-mails, instant messages, and passwords typed into a web browser.18 Furthermore, RCS can turn on a device?s webcam and microphone to spy on the user.19
While Hacking Team claims to potential clients that RCS can be used for mass surveillance of ?hundreds of thousands of targets?,20public statements by Hacking Team emphasize RCS?s potential use as a targeted tool for fighting crime and terrorism.21
Hacking Team was first thrust into the public spotlight in 2012 when RCS was used against award-winning Moroccan media outlet Mamfakinch,22 and UAE human rights activist Ahmed Mansoor, who was pardoned23 after serving seven months in prison for signing an online pro-democracy petition.24 Mansoor was infected, his GMail password was stolen, and his e-mails were downloaded.25 At the same time, RCS is apparently being used by foreign governments to target individuals on US soil.26,27
Evidence of the use of RCS against journalists and activists led Reporters Without Borders to name Hacking Team as one of the five ?Corporate Enemies of the Internet?.28 Hacking Team Senior Counsel Eric Rabe responded with a defense of his company?s sales practices, in which he stated that Hacking Team does not provide its products to ?repressive? regimes.29
On the issue of repressive regimes, Hacking Team goes to great lengths to assure that our software is not sold to governments that are blacklisted by the E.U., the U.S.A., NATO and similar international organizations or any ?repressive? regime.
?Repressive? is a subjective term that may be difficult to define. We instead look to a selection of publications that rank countries based on freedom and democracy using a methodology. For example, The Economist publishes a Democracy Index,30 which rates governments around the world on a spectrum from ?full democracies? to ?authoritarian regimes.? Reporters Without Borders also publishes a yearly Press Freedom Index, which ranks countries? press freedom situations from ?good? to ?very serious?.31
Ethiopia and Ethiopian Satellite Television Service (ESAT)
The Economist ranks Ethiopia as an ?authoritarian regime,? and Reporters Without Borders classifies it as a country where there is a ?difficult situation? for journalists. Human Rights Watch calls Ethiopia?s press law ?deeply flawed,? and notes that several award-winning journalists have been convicted under the law for exercising their right to freedom of expression, as part of a government crackdown on independent media.32
Journalists jailed under the law include Eskinder Nega, who was convicted of terrorism in 2012 in a case following the publication of his column that criticized the government?s detention of journalists.33 Nega won the 2012 PEN America Freedom to Write Award, and was hailed by the group as of the ?bravest and most admirable of writers, one who picked up his pen to write things that he knew would surely put him at grave risk?.34 Nega is currently serving an 18 year sentence in prison, having ?[fallen] victim to exactly the measures he was highlighting?.35 In a May 2013 letter from prison, he wrote, ?I will live to see the light at the end of the tunnel. It may or may not be a long wait. Whichever way events may go, I shall persevere!?36
ESAT describes itself as ?powered by broad-based collective of exiled journalists, human rights advocates, civic society leaders and members in the Diaspora.? Available in Ethiopia around the world, ESAT?s television and radio signals have been subjected to jamming from within Ethiopia several times in the past few years.37
Previous research by the Citizen Lab found a version of the FinFisher government spyware that used a picture of members of Ethiopian opposition group Ginbot 7 as bait, indicating politically-motivated targeting. That spyware communicated with a command and control server in Ethiopia.38
First Targeting Attempt
First, the ESATSTUDIO Skype account was targeted with spyware. This account is used by ESAT for on-air interviews. The individual operating the ESATSTUDIO account at the time was an ESAT employee in Belgium, responsible for managing ESAT?s satellite broadcasts. An individual identified as ?Yalfalkenu Meches? (Skype: yalfalkenu1) sent a file to ESATSTUDIO entitled ?An Article for ESAT.rar.? We use Skype logs provided by the targets to illustrate the attacks.
This .rar file contained an .exe file disguised as a .pdf. The file used the Adobe PDF icon, and contained a large number of spaces between the name and extension, to prevent Windows from displaying the extension.
Left: How the file was rendered in Windows; Right: Windows file properties dialog
Despite the file?s name, ?An Article for ESAT,? the file did not display any such article, or any other content, when opened.
Analysis and Link to Hacking Team RCS
Summary
The file sent to ESAT appeared to be Hacking Team?s RCS spyware for the following two reasons:
The file communicated with a server that returned two SSL certificates. The second certificate was issued by ?RCS Certification Authority? / ?HT srl?, and was similar to SSL certificates returned by two other servers apparently owned by Hacking Team. The first certificate was similar to certificates returned by two other servers that appeared to be demonstration servers for Hacking Team?s RCS spyware.
The file matched a signature that we had previously developed for RCS spyware.
Detailed Analysis
The hash of the file was:
sha256: 4a53db7b98aa000aeaa72d6a44004ef9ed3b6c09dd04a3e6015b62d741de3437
sha1: b7438e699dd54f8b56fc779c1b8b08b1943d9892
md5: 53a9e1b59ff37cc2aeff0391cc546201
Shortly after opening the .exe file, it attempted to communicate with the server 46.4.69.25 on port 80.
inetnum: 46.4.69.0 - 46.4.69.31
netname: HETZNER-RZ14
descr: Hetzner Online AG
descr: Datacenter 14
country: DE
We probed the server and noticed that it returned two self-signed SSL certificates:39
Issuer Subject Fingerprint
/CN=default /CN=server a7c0eacd845a7a433eca76f7d42fc3fedf1bde3c
/CN=RCS Certification Authority /O=HT srl /CN=RCS Certification Authority /O=HT srl 6500c243015a6ecc59f1272fec38eb0065d22063
The second certificate is issued by ?RCS Certification Authority? / ?HT srl?.Hacking Team refers to their spyware as ?RCS,? and identifies itself as ?HT S.r.l.? on its website:
To confirm our hypothesis that these certificates were associated with Hacking Team, we searched historical SSL certificate data released by the Internet Census40 (443-TCP_SSLSessionReq) and by the University of Michigan?s zmap project.41 We found two servers returning the ?RCS Certification Authority? / ?HT srl? certificate that were in the following range:
inetnum: 93.62.139.32 - 93.62.139.47
netname: FASTWEB-HT
descr: HT public subnet
country: IT
person: GIANCARLO RUSSO
address: VIA DELLA MOSCOVA 13
address: MILANO MI
address: IT
phone: +39 0229060603
The address and phone number on the range matches those on Hacking Team?s website. A Giancarlo Russo is listed as the COO of Hacking Team on LinkedIn.42 Thus, we believe that Hacking Team controls this range of IP addresses.
The two servers in this range that returned similar certificates to the server in the ESAT spyware were:
93.62.139.39 on 6/28/2012:
Issuer Subject Fingerprint
/CN=RCS Certification Authority /O=HT srl /CN=rcs-castore deee895bf1f68e97cb997d929e0f991ecec6ab29
/CN=RCS Certification Authority /O=HT srl /CN=RCS Certification Authority /O=HT srl 1e8e8806aa605544cda2bbb906b5d0cc7fb6fff7
93.62.139.42 on 8/12/2012:
Issuer Subject Fingerprint
/CN=RCS Certification Authority /O=HT srl /CN=rcs-polluce 277fdf33df7baca54ce8336982db865d9f38f514
/CN=RCS Certification Authority /O=HT srl /CN=RCS Certification Authority /O=HT srl e8d5f17d142768abe2ed835d5a61d99602ab082b
Because these IP addresses were registered to Hacking Team, we believe that the presence of a certificate apparently issued by ?RCS Certification Authority? / ?HT srl? is indicative of a server for Hacking Team?s RCS spyware. The Internet Census (443-TCP_SSLSessionReq) also recorded two instances of a server returning a certificate that matched the ?default? / ?server? certificate returned by the server in the ESAT spyware, along with an incomplete certificate for ?rcs-demo.hackingteam.it?. This server was used by an RCS spyware sample found in VirusTotal.43 This certificate was returned by 168.144.159.167 on 12/14/2012, and by 94.199.243.39 on 12/14/2012. This is a further indication that the server in the spyware targeting ESAT is a Hacking Team RCS server.
The file itself also matched a signature we had previously developed for RCS spyware.
Second Attempt
The target did not open the first file (?An Article for ESAT.exe?), and complained to Yalfalkenu that the file was an .exe application. Yalfalkenu responded that he had received the file from a friend.
Yalfalkenu also said that he opened the .exe file and it ?worked fine.? However, despite the file?s name, ?An Article for ESAT,? the file did not display any such article, or any other content, when opened.
Yalfalkenu followed up by sending ESATSTUDIO a Word document.
Analysis and Link to Hacking Team RCS
The Word document was:
sha256: 5bde4288c11f0701b54398ffeeddb4d6882d91b3e34bf76b1e250b8fc46be11d
sha1: 057675f8dfda0f44a695ec18a5211ff4e68a1873
md5: 8df850088e2324d5c89615be32bd8a35
As with the previous file, opening this file did not result in any bait content being displayed. A user who opened the file saw a blank Word document, which quickly closed itself.
The document exploited a bug in Microsoft Windows (CVE-2012-015844) to run a program that downloaded and executed a file: 216.118.232.254/svchst.exe. An update to Windows available since April 2012 fixes this bug.45 The IP address 216.118.232.254 belongs to Ariave Satcom, a satellite provider that services Africa, Europe, and Asia.46
Private Customer VSC-ARIAVE (NET-216-118-232-0-1) 216.118.232.0 - 216.118.232.255
VSC Satellite Co. VSC-IPOWN1 (NET-216-118-224-0-1) 216.118.224.0 - 216.118.255.255
We downloaded svchst.exe:
sha256: bc68c8d86f2522fb4c58c6f482c5cacb284e5ef803d41a63142677855934d969
sha1: b341cc1c299c07624814f35a35a4d505e65d3b67
md5: 015c238d56b8657c0946ec45b131362a
Like the first file, the file communicated with 46.4.69.25. This file also matched our signature for RCS spyware. For the same reasons as the first file, this file appears to be Hacking Team RCS spyware.
Third Attempt
An hour and a half later on the same day,47 Yalfalkenu targeted another ESAT employee, this time based in their Northern Virginia offices.
The document was:
sha256: 8f9a6ae6aa56e12596d02c864998b4373a96d3f788195db3601b6e3ec54a99fb
sha1: c384ca066fe0145455f14976c0ecf8a817a30f86
md5: daa5912d4ca0e4a143378947ef329374
Like the second file, the document also exploited the CVE-2012-0158 bug, but had two main differences. First, the document actually displayed bait content ? a copy of this article.48 Second, instead of downloading a file from a server, the document contained an embedded file, which it copied as CyHidWin.exe. We extracted the file and analyzed it:
sha256: d30bc31d6ad75de20aa3a45d338298030dc9136ba94aee93b4843e279fa3d59c
sha1: 4f8b2f1071870b9d03f3bb341cf9523b0574d8f6
md5: c5cfa1afd5d3148a0d33fc1940ea1a37
As in the previous two files, the file communicated with 46.4.69.25. This file also matched our signature for RCS spyware. For the same reasons as the first two files, this file appears to be Hacking Team RCS spyware.
Epilogue
After the first two targeting attempts, we alerted ESAT that Yalfalkenu Meches was trying to target them with spyware. On the third attempt, the targeted user confronted Yalfalkenu, who again professed that he had received the file from a friend.
Yalfalkenu also expressed puzzlement about how opening a Word document could infect a computer, and said that he was a victim.
We talked to employees of ESAT, who said that Yalfalkenu used to collaborate with them, but then he ?disappeared for a while.? It is possible that someone else is now using Yalfalkenu?s account.
Links to Other Spyware
Our scans indicated that the following other servers were likely being run by the same attacker that targeted ESAT, and were also likely Hacking Team RCS servers:
IP First Seen Last Seen Provider Country
109.200.22.160 7/25/2012 8/10/2012 Delamere Services UK
109.200.22.161 7/25/2012 8/12/2012 Delamere Services UK
109.200.22.162 10/14/2012 1/13/2014 Delamere Services UK
109.200.22.163 10/13/2012 1/13/2014 Delamere Services UK
176.74.178.45 10/30/2013 1/13/2014 Infinite Dimension Solutions UK
176.74.178.119 7/25/2012 8/12/2012 Infinite Dimension Solutions UK
176.74.178.120 7/25/2012 8/12/2012 Infinite Dimension Solutions UK
176.74.178.202 10/13/2012 1/13/2014 Infinite Dimension Solutions UK
176.74.178.203 10/18/2012 1/13/2014 Infinite Dimension Solutions UK
46.166.162.147 5/16/2013 8/11/2013 Santrex SC
69.60.98.203 5/16/2013 Active Serverpronto US
216.118.232.245 11/18/2013 Active Ariave Satcom ??
We note that the ?RCS Certification Authority? / ?HT srl? SSL certificates returned by these servers were issued on 5/8/2012. Based on this date, we estimate that the attacker who targeted ESAT has been using Hacking Team?s RCS spyware since May 2012, or earlier.
We found the following sample in VirusTotal that matched our signature for Hacking Team RCS spyware. The sample used 46.166.162.147 as a command and control server. Thus, we believe the attackers were the same, though we have no indication as to who they may have targeted:
sha256: 9577aabf5e31af1409e2abe8c29ac918d7f8784dec75b4088a60fce6a45e9fc7
sha1: 0e326c39c91efeff1d045bec3c7e7c38405d0430
md5: c17e788e28d47891f94c64739ee7fffb
Conclusion
In this report, we identified three instances where Ethiopian journalist group ESAT was targeted with spyware in the space of two hours by a single attacker. In each case the spyware appeared to be RCS (Remote Control System), programmed and sold exclusively to governments by Milan-based Hacking Team. While Hacking Team and other ?lawful intercept? spyware vendors purport to practice effective self-regulation, this case seems to be part of a broader pattern of government abuse of such spyware. ?Lawful intercept? spyware has also apparently been abused to target Bahraini activists, Moroccan journalists, critics of the Turkish Government, and Emirati human rights activists.
Acknowledgements
Thanks to Eva Galperin, the Electronic Frontier Foundation, and ESAT.
Footnotes
1 http://ethsat.com/
2 http://ethsat.com/about-us/
3 http://ethsat.com/2011/10/08/esat-accuses-china-of-complicity-in-jamming-signals/
4 http://ethsat.com/2014/01/09/udj-says-expressing-opinion-to-media-is-not-terror/
5 https://web.archive.org/web/20130723051052/http://ariave.com/tech.htm
6 http://hackingteam.it/index.php/customer-policy
7 http://news.cnet.com/8301-13578_3-57573707-38/meet-the-corporate-enemies-of-the-internet-for-2013/
8 http://www.eluniverso.com/noticias/2013/12/11/nota/1901271/firma-hacking-team-fue-contactada-estado-ecuatoriano
9 http://www.ibtimes.co.uk/hacking-team-murky-world-state-sponsored-spying-445507
10 http://hackingteam.it/index.php/customer-policy
11 http://www.cpj.org/2013/11/ethiopia-arrests-2-journalists-from-independent-pa.php
12 http://www.hrw.org/world-report/2013/country-chapters/ethiopia
13 http://www.hrw.org/node/119814/section/2
14 http://www.hrw.org/world-report/2013/country-chapters/ethiopia?page=3
15 ibid.
16 http://hackingteam.it/index.php/remote-control-system
17 http://wikileaks.org/spyfiles/docs/hackingteam/147_remote-control-system.html
18 https://www.securelist.com/en/analysis/204792290/Spyware_HackingTeam
19 http://www.theverge.com/2013/9/13/4723610/meet-hacking-team-the-company-that-helps-police-hack-into-computers
20 ibid.
21 http://www.corpwatch.org/article.php?id=15868
22 http://slate.me/1eSTeUF
23 http://en.rsf.org/united-arab-emirates-ahmed-mansoor-and-four-other-pro-28-11-2011,41477.html
24 http://www.bbc.co.uk/news/world-middle-east-13043270
25 https://citizenlab.org/2012/10/backdoors-are-forever-hacking-team-and-the-targeting-of-dissent/
26 http://www.wired.com/threatlevel/2013/06/spy-tool-sold-to-governments/
27 https://twitter.com/csoghoian/status/298899565388644352
28 http://surveillance.rsf.org/en/category/corporate-enemies/
29 http://news.cnet.com/8301-13578_3-57573707-38/meet-the-corporate-enemies-of-the-internet-for-2013/
30 https://www.eiu.com/public/topical_report.aspx?campaignid=DemocracyIndex12
31 Loading Image...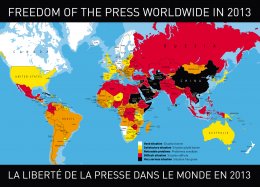
32 http://www.hrw.org/news/2013/05/03/ethiopia-terrorism-law-decimates-media
33 http://www.bbc.co.uk/news/world-africa-17921950
34 http://www.pen.org/press-release/2012/04/12/top-pen-prize-honor-eskinder-nega-jailed-ethiopian-journalist-and-blogger
35 ibid.
36 https://www.amnesty.org/en/appeals-for-action/LWM2013-Ethiopia
37 http://ethsat.com/2011/10/08/esat-accuses-china-of-complicity-in-jamming-signals/
38 https://citizenlab.org/2013/03/you-only-click-twice-finfishers-global-proliferation-2/
39 This can be verified by consulting the Sonar SSL scans (https://scans.io/study/sonar.ssl) between 10/30/2013 and 1/13/2014.
40 http://internetcensus2012.bitbucket.org/paper.html
41 https://scans.io/study/umich-https
42 http://it.linkedin.com/pub/giancarlo-russo/2/2a9/589
43 https://www.virustotal.com/en/file/81e9647a3371568cddd0a4db597de8423179773d910d9a7b3d945cb2c3b7e1c2/analysis/
44 http://www.cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2012-0158
45 http://technet.microsoft.com/en-us/security/bulletin/ms12-027
46 https://web.archive.org/web/20130723051052/http://ariave.com/tech.htm
47 On 20 December 2013, Belgium?s time zone was 6 hours ahead of Northern Virginia?s.
48 The article quotes the former head of Ethiopia?s Amhara region (Ayalew Gobeze) as denying that he was demoted or fired for failing to sign a border demarcation agreement between Sudan and Ethiopia. Ayalew is quoted as saying that members of the Ethiopian diaspora concocted the story, and refers to them as ?taxi drivers? and ?jobless?.
Ronald Deibert
Director, the Citizen Lab
and the Canada Centre for Global Security Studies
Munk School of Global Affairs
University of Toronto
(416) 946-8916
PGP: http://deibert.citizenlab.org/pubkey.txt
http://deibert.citizenlab.org/
twitter.com/citizenlab
r.deibert at utoronto.ca
-------------- next part --------------
An HTML attachment was scrubbed...
URL: <http://mailman.stanford.edu/pipermail/liberationtech/attachments/20140212/5823463d/attachment-0001.html>
On behalf of the Citizen Lab, I am pleased to announce a new publication, details for which are below. This report is the first in a series that focus
on the global proliferation and use of Hacking Team's RCS spyware, sold exclusively to governments. More posts will follow in the next week.
The report is authored by Bill Marczak, Claudio Guarnieri, Morgan Marquis-Boire, and John Scott-Railton. I'd like to draw attention to the innovative
mixed scanning methods developed in this post, around which a new field of research is emerging which I believe is going to be critical to the
type of distributed civil controls on the global spyware market.
Regards
Ron
https://citizenlab.org/2014/02/hackingteam-targeting-ethiopian-journalists/
Hacking Team and the Targeting of Ethiopian Journalists
February 12, 2014
Tagged: Ethiopia, Hacking Team
Categories: News and Announcements, Reports and Briefings, Research News
Authors: Bill Marczak, Claudio Guarnieri, Morgan Marquis-Boire, and John Scott-Railton.
This post is the first in a series of posts that focus on the global proliferation and use of Hacking Team?s RCS spyware, sold exclusively to governments.
Summary
Ethiopian Satellite Television Service1 (ESAT) is an independent satellite television, radio, and online news media outlet run by members of the Ethiopian diaspora. The service has operations in Alexandria, Virginia, as well as several other countries.2 ESAT?s broadcasts are frequently critical of the Ethiopian Government. Available in Ethiopia and around the world, ESAT has been subjected to jamming from within Ethiopia several times in the past few years.3 A recent documentary shown on Ethiopian state media warned opposition parties against participating in ESAT programming.4
In the space of two hours on 20 December 2013, an attacker made three separate attempts to target two ESAT employees with sophisticated computer spyware, designed to steal files and passwords, and intercept Skype calls and instant messages. The spyware communicated with an IP address belonging to Ariave Satcom, a satellite provider that services Africa, Europe, and Asia.5 In each case, the spyware appeared to be Remote Control System (RCS), sold exclusively to governments by Milan-based Hacking Team.6
Hacking Team states that they do not sell RCS to ?repressive regimes?,7 and that RCS is not sold through ?independent agents?.8 Hacking Team also says that all sales are reviewed by a board that includes outside engineers and lawyers. The board has veto power over any sale.9 Before authorizing a sale, the company states that it considers ?credible government or non-government reports reflecting that a potential customer could use surveillance technologies to facilitate human rights abuses,? as well as ?due process requirements? for surveillance.10
The Committee to Protect Journalists (CPJ) reports that Ethiopia jails more journalists than any other African country besides Eritrea, and says that the Ethiopian government has shut down more than 75 media outlets since 1993.11 CPJ statistics also show that 79 journalists have been forced to flee Ethiopia due to threats and intimidation over the past decade, more than any other country in the world.12 A 2013 Human Rights Watch (HRW) report detailed ongoing torture at Ethiopia?s Maekelawi detention center, the first stop for arrested journalists and protests organizers. Former detainees described how they were: ?repeatedly slapped, kicked, punched, and beaten,? and hung from the ceiling by their wrists. Information extracted in confession has been used to obtain conviction at trial, and to compel former detainees to work with the government.13 HRW also indicated abuses committed by the army, including the use of torture and rape to compel information from villagers near the site of an attack on a farm.14 HRW noted ?insufficient respect for ? due process? in Ethiopia.15
Background
Hacking Team and Remote Control System (RCS)
Hacking Team, also known as HT S.r.l., is a Milan-based purveyor of ?offensive technology? to governments around the world. One of their products, known as Remote Control System (RCS), is a trojan that is sold exclusively to intelligence and law enforcement agencies worldwide. Hacking Team?s website describes the product as ?the solution? to monitor targets that are increasingly using encryption, or those located outside the borders of the government that wants to monitor them.16
Description of RCS in a 2011 official brochure.17
RCS infects a target?s computer or mobile phone to intercept data before it is encrypted for transmission, and can also intercept data that is never transmitted. For example, it can copy files from a computer?s hard disk, and can also record Skype calls, e-mails, instant messages, and passwords typed into a web browser.18 Furthermore, RCS can turn on a device?s webcam and microphone to spy on the user.19
While Hacking Team claims to potential clients that RCS can be used for mass surveillance of ?hundreds of thousands of targets?,20public statements by Hacking Team emphasize RCS?s potential use as a targeted tool for fighting crime and terrorism.21
Hacking Team was first thrust into the public spotlight in 2012 when RCS was used against award-winning Moroccan media outlet Mamfakinch,22 and UAE human rights activist Ahmed Mansoor, who was pardoned23 after serving seven months in prison for signing an online pro-democracy petition.24 Mansoor was infected, his GMail password was stolen, and his e-mails were downloaded.25 At the same time, RCS is apparently being used by foreign governments to target individuals on US soil.26,27
Evidence of the use of RCS against journalists and activists led Reporters Without Borders to name Hacking Team as one of the five ?Corporate Enemies of the Internet?.28 Hacking Team Senior Counsel Eric Rabe responded with a defense of his company?s sales practices, in which he stated that Hacking Team does not provide its products to ?repressive? regimes.29
On the issue of repressive regimes, Hacking Team goes to great lengths to assure that our software is not sold to governments that are blacklisted by the E.U., the U.S.A., NATO and similar international organizations or any ?repressive? regime.
?Repressive? is a subjective term that may be difficult to define. We instead look to a selection of publications that rank countries based on freedom and democracy using a methodology. For example, The Economist publishes a Democracy Index,30 which rates governments around the world on a spectrum from ?full democracies? to ?authoritarian regimes.? Reporters Without Borders also publishes a yearly Press Freedom Index, which ranks countries? press freedom situations from ?good? to ?very serious?.31
Ethiopia and Ethiopian Satellite Television Service (ESAT)
The Economist ranks Ethiopia as an ?authoritarian regime,? and Reporters Without Borders classifies it as a country where there is a ?difficult situation? for journalists. Human Rights Watch calls Ethiopia?s press law ?deeply flawed,? and notes that several award-winning journalists have been convicted under the law for exercising their right to freedom of expression, as part of a government crackdown on independent media.32
Journalists jailed under the law include Eskinder Nega, who was convicted of terrorism in 2012 in a case following the publication of his column that criticized the government?s detention of journalists.33 Nega won the 2012 PEN America Freedom to Write Award, and was hailed by the group as of the ?bravest and most admirable of writers, one who picked up his pen to write things that he knew would surely put him at grave risk?.34 Nega is currently serving an 18 year sentence in prison, having ?[fallen] victim to exactly the measures he was highlighting?.35 In a May 2013 letter from prison, he wrote, ?I will live to see the light at the end of the tunnel. It may or may not be a long wait. Whichever way events may go, I shall persevere!?36
ESAT describes itself as ?powered by broad-based collective of exiled journalists, human rights advocates, civic society leaders and members in the Diaspora.? Available in Ethiopia around the world, ESAT?s television and radio signals have been subjected to jamming from within Ethiopia several times in the past few years.37
Previous research by the Citizen Lab found a version of the FinFisher government spyware that used a picture of members of Ethiopian opposition group Ginbot 7 as bait, indicating politically-motivated targeting. That spyware communicated with a command and control server in Ethiopia.38
First Targeting Attempt
First, the ESATSTUDIO Skype account was targeted with spyware. This account is used by ESAT for on-air interviews. The individual operating the ESATSTUDIO account at the time was an ESAT employee in Belgium, responsible for managing ESAT?s satellite broadcasts. An individual identified as ?Yalfalkenu Meches? (Skype: yalfalkenu1) sent a file to ESATSTUDIO entitled ?An Article for ESAT.rar.? We use Skype logs provided by the targets to illustrate the attacks.
This .rar file contained an .exe file disguised as a .pdf. The file used the Adobe PDF icon, and contained a large number of spaces between the name and extension, to prevent Windows from displaying the extension.
Left: How the file was rendered in Windows; Right: Windows file properties dialog
Despite the file?s name, ?An Article for ESAT,? the file did not display any such article, or any other content, when opened.
Analysis and Link to Hacking Team RCS
Summary
The file sent to ESAT appeared to be Hacking Team?s RCS spyware for the following two reasons:
The file communicated with a server that returned two SSL certificates. The second certificate was issued by ?RCS Certification Authority? / ?HT srl?, and was similar to SSL certificates returned by two other servers apparently owned by Hacking Team. The first certificate was similar to certificates returned by two other servers that appeared to be demonstration servers for Hacking Team?s RCS spyware.
The file matched a signature that we had previously developed for RCS spyware.
Detailed Analysis
The hash of the file was:
sha256: 4a53db7b98aa000aeaa72d6a44004ef9ed3b6c09dd04a3e6015b62d741de3437
sha1: b7438e699dd54f8b56fc779c1b8b08b1943d9892
md5: 53a9e1b59ff37cc2aeff0391cc546201
Shortly after opening the .exe file, it attempted to communicate with the server 46.4.69.25 on port 80.
inetnum: 46.4.69.0 - 46.4.69.31
netname: HETZNER-RZ14
descr: Hetzner Online AG
descr: Datacenter 14
country: DE
We probed the server and noticed that it returned two self-signed SSL certificates:39
Issuer Subject Fingerprint
/CN=default /CN=server a7c0eacd845a7a433eca76f7d42fc3fedf1bde3c
/CN=RCS Certification Authority /O=HT srl /CN=RCS Certification Authority /O=HT srl 6500c243015a6ecc59f1272fec38eb0065d22063
The second certificate is issued by ?RCS Certification Authority? / ?HT srl?.Hacking Team refers to their spyware as ?RCS,? and identifies itself as ?HT S.r.l.? on its website:
To confirm our hypothesis that these certificates were associated with Hacking Team, we searched historical SSL certificate data released by the Internet Census40 (443-TCP_SSLSessionReq) and by the University of Michigan?s zmap project.41 We found two servers returning the ?RCS Certification Authority? / ?HT srl? certificate that were in the following range:
inetnum: 93.62.139.32 - 93.62.139.47
netname: FASTWEB-HT
descr: HT public subnet
country: IT
person: GIANCARLO RUSSO
address: VIA DELLA MOSCOVA 13
address: MILANO MI
address: IT
phone: +39 0229060603
The address and phone number on the range matches those on Hacking Team?s website. A Giancarlo Russo is listed as the COO of Hacking Team on LinkedIn.42 Thus, we believe that Hacking Team controls this range of IP addresses.
The two servers in this range that returned similar certificates to the server in the ESAT spyware were:
93.62.139.39 on 6/28/2012:
Issuer Subject Fingerprint
/CN=RCS Certification Authority /O=HT srl /CN=rcs-castore deee895bf1f68e97cb997d929e0f991ecec6ab29
/CN=RCS Certification Authority /O=HT srl /CN=RCS Certification Authority /O=HT srl 1e8e8806aa605544cda2bbb906b5d0cc7fb6fff7
93.62.139.42 on 8/12/2012:
Issuer Subject Fingerprint
/CN=RCS Certification Authority /O=HT srl /CN=rcs-polluce 277fdf33df7baca54ce8336982db865d9f38f514
/CN=RCS Certification Authority /O=HT srl /CN=RCS Certification Authority /O=HT srl e8d5f17d142768abe2ed835d5a61d99602ab082b
Because these IP addresses were registered to Hacking Team, we believe that the presence of a certificate apparently issued by ?RCS Certification Authority? / ?HT srl? is indicative of a server for Hacking Team?s RCS spyware. The Internet Census (443-TCP_SSLSessionReq) also recorded two instances of a server returning a certificate that matched the ?default? / ?server? certificate returned by the server in the ESAT spyware, along with an incomplete certificate for ?rcs-demo.hackingteam.it?. This server was used by an RCS spyware sample found in VirusTotal.43 This certificate was returned by 168.144.159.167 on 12/14/2012, and by 94.199.243.39 on 12/14/2012. This is a further indication that the server in the spyware targeting ESAT is a Hacking Team RCS server.
The file itself also matched a signature we had previously developed for RCS spyware.
Second Attempt
The target did not open the first file (?An Article for ESAT.exe?), and complained to Yalfalkenu that the file was an .exe application. Yalfalkenu responded that he had received the file from a friend.
Yalfalkenu also said that he opened the .exe file and it ?worked fine.? However, despite the file?s name, ?An Article for ESAT,? the file did not display any such article, or any other content, when opened.
Yalfalkenu followed up by sending ESATSTUDIO a Word document.
Analysis and Link to Hacking Team RCS
The Word document was:
sha256: 5bde4288c11f0701b54398ffeeddb4d6882d91b3e34bf76b1e250b8fc46be11d
sha1: 057675f8dfda0f44a695ec18a5211ff4e68a1873
md5: 8df850088e2324d5c89615be32bd8a35
As with the previous file, opening this file did not result in any bait content being displayed. A user who opened the file saw a blank Word document, which quickly closed itself.
The document exploited a bug in Microsoft Windows (CVE-2012-015844) to run a program that downloaded and executed a file: 216.118.232.254/svchst.exe. An update to Windows available since April 2012 fixes this bug.45 The IP address 216.118.232.254 belongs to Ariave Satcom, a satellite provider that services Africa, Europe, and Asia.46
Private Customer VSC-ARIAVE (NET-216-118-232-0-1) 216.118.232.0 - 216.118.232.255
VSC Satellite Co. VSC-IPOWN1 (NET-216-118-224-0-1) 216.118.224.0 - 216.118.255.255
We downloaded svchst.exe:
sha256: bc68c8d86f2522fb4c58c6f482c5cacb284e5ef803d41a63142677855934d969
sha1: b341cc1c299c07624814f35a35a4d505e65d3b67
md5: 015c238d56b8657c0946ec45b131362a
Like the first file, the file communicated with 46.4.69.25. This file also matched our signature for RCS spyware. For the same reasons as the first file, this file appears to be Hacking Team RCS spyware.
Third Attempt
An hour and a half later on the same day,47 Yalfalkenu targeted another ESAT employee, this time based in their Northern Virginia offices.
The document was:
sha256: 8f9a6ae6aa56e12596d02c864998b4373a96d3f788195db3601b6e3ec54a99fb
sha1: c384ca066fe0145455f14976c0ecf8a817a30f86
md5: daa5912d4ca0e4a143378947ef329374
Like the second file, the document also exploited the CVE-2012-0158 bug, but had two main differences. First, the document actually displayed bait content ? a copy of this article.48 Second, instead of downloading a file from a server, the document contained an embedded file, which it copied as CyHidWin.exe. We extracted the file and analyzed it:
sha256: d30bc31d6ad75de20aa3a45d338298030dc9136ba94aee93b4843e279fa3d59c
sha1: 4f8b2f1071870b9d03f3bb341cf9523b0574d8f6
md5: c5cfa1afd5d3148a0d33fc1940ea1a37
As in the previous two files, the file communicated with 46.4.69.25. This file also matched our signature for RCS spyware. For the same reasons as the first two files, this file appears to be Hacking Team RCS spyware.
Epilogue
After the first two targeting attempts, we alerted ESAT that Yalfalkenu Meches was trying to target them with spyware. On the third attempt, the targeted user confronted Yalfalkenu, who again professed that he had received the file from a friend.
Yalfalkenu also expressed puzzlement about how opening a Word document could infect a computer, and said that he was a victim.
We talked to employees of ESAT, who said that Yalfalkenu used to collaborate with them, but then he ?disappeared for a while.? It is possible that someone else is now using Yalfalkenu?s account.
Links to Other Spyware
Our scans indicated that the following other servers were likely being run by the same attacker that targeted ESAT, and were also likely Hacking Team RCS servers:
IP First Seen Last Seen Provider Country
109.200.22.160 7/25/2012 8/10/2012 Delamere Services UK
109.200.22.161 7/25/2012 8/12/2012 Delamere Services UK
109.200.22.162 10/14/2012 1/13/2014 Delamere Services UK
109.200.22.163 10/13/2012 1/13/2014 Delamere Services UK
176.74.178.45 10/30/2013 1/13/2014 Infinite Dimension Solutions UK
176.74.178.119 7/25/2012 8/12/2012 Infinite Dimension Solutions UK
176.74.178.120 7/25/2012 8/12/2012 Infinite Dimension Solutions UK
176.74.178.202 10/13/2012 1/13/2014 Infinite Dimension Solutions UK
176.74.178.203 10/18/2012 1/13/2014 Infinite Dimension Solutions UK
46.166.162.147 5/16/2013 8/11/2013 Santrex SC
69.60.98.203 5/16/2013 Active Serverpronto US
216.118.232.245 11/18/2013 Active Ariave Satcom ??
We note that the ?RCS Certification Authority? / ?HT srl? SSL certificates returned by these servers were issued on 5/8/2012. Based on this date, we estimate that the attacker who targeted ESAT has been using Hacking Team?s RCS spyware since May 2012, or earlier.
We found the following sample in VirusTotal that matched our signature for Hacking Team RCS spyware. The sample used 46.166.162.147 as a command and control server. Thus, we believe the attackers were the same, though we have no indication as to who they may have targeted:
sha256: 9577aabf5e31af1409e2abe8c29ac918d7f8784dec75b4088a60fce6a45e9fc7
sha1: 0e326c39c91efeff1d045bec3c7e7c38405d0430
md5: c17e788e28d47891f94c64739ee7fffb
Conclusion
In this report, we identified three instances where Ethiopian journalist group ESAT was targeted with spyware in the space of two hours by a single attacker. In each case the spyware appeared to be RCS (Remote Control System), programmed and sold exclusively to governments by Milan-based Hacking Team. While Hacking Team and other ?lawful intercept? spyware vendors purport to practice effective self-regulation, this case seems to be part of a broader pattern of government abuse of such spyware. ?Lawful intercept? spyware has also apparently been abused to target Bahraini activists, Moroccan journalists, critics of the Turkish Government, and Emirati human rights activists.
Acknowledgements
Thanks to Eva Galperin, the Electronic Frontier Foundation, and ESAT.
Footnotes
1 http://ethsat.com/
2 http://ethsat.com/about-us/
3 http://ethsat.com/2011/10/08/esat-accuses-china-of-complicity-in-jamming-signals/
4 http://ethsat.com/2014/01/09/udj-says-expressing-opinion-to-media-is-not-terror/
5 https://web.archive.org/web/20130723051052/http://ariave.com/tech.htm
6 http://hackingteam.it/index.php/customer-policy
7 http://news.cnet.com/8301-13578_3-57573707-38/meet-the-corporate-enemies-of-the-internet-for-2013/
8 http://www.eluniverso.com/noticias/2013/12/11/nota/1901271/firma-hacking-team-fue-contactada-estado-ecuatoriano
9 http://www.ibtimes.co.uk/hacking-team-murky-world-state-sponsored-spying-445507
10 http://hackingteam.it/index.php/customer-policy
11 http://www.cpj.org/2013/11/ethiopia-arrests-2-journalists-from-independent-pa.php
12 http://www.hrw.org/world-report/2013/country-chapters/ethiopia
13 http://www.hrw.org/node/119814/section/2
14 http://www.hrw.org/world-report/2013/country-chapters/ethiopia?page=3
15 ibid.
16 http://hackingteam.it/index.php/remote-control-system
17 http://wikileaks.org/spyfiles/docs/hackingteam/147_remote-control-system.html
18 https://www.securelist.com/en/analysis/204792290/Spyware_HackingTeam
19 http://www.theverge.com/2013/9/13/4723610/meet-hacking-team-the-company-that-helps-police-hack-into-computers
20 ibid.
21 http://www.corpwatch.org/article.php?id=15868
22 http://slate.me/1eSTeUF
23 http://en.rsf.org/united-arab-emirates-ahmed-mansoor-and-four-other-pro-28-11-2011,41477.html
24 http://www.bbc.co.uk/news/world-middle-east-13043270
25 https://citizenlab.org/2012/10/backdoors-are-forever-hacking-team-and-the-targeting-of-dissent/
26 http://www.wired.com/threatlevel/2013/06/spy-tool-sold-to-governments/
27 https://twitter.com/csoghoian/status/298899565388644352
28 http://surveillance.rsf.org/en/category/corporate-enemies/
29 http://news.cnet.com/8301-13578_3-57573707-38/meet-the-corporate-enemies-of-the-internet-for-2013/
30 https://www.eiu.com/public/topical_report.aspx?campaignid=DemocracyIndex12
31 Loading Image...
32 http://www.hrw.org/news/2013/05/03/ethiopia-terrorism-law-decimates-media
33 http://www.bbc.co.uk/news/world-africa-17921950
34 http://www.pen.org/press-release/2012/04/12/top-pen-prize-honor-eskinder-nega-jailed-ethiopian-journalist-and-blogger
35 ibid.
36 https://www.amnesty.org/en/appeals-for-action/LWM2013-Ethiopia
37 http://ethsat.com/2011/10/08/esat-accuses-china-of-complicity-in-jamming-signals/
38 https://citizenlab.org/2013/03/you-only-click-twice-finfishers-global-proliferation-2/
39 This can be verified by consulting the Sonar SSL scans (https://scans.io/study/sonar.ssl) between 10/30/2013 and 1/13/2014.
40 http://internetcensus2012.bitbucket.org/paper.html
41 https://scans.io/study/umich-https
42 http://it.linkedin.com/pub/giancarlo-russo/2/2a9/589
43 https://www.virustotal.com/en/file/81e9647a3371568cddd0a4db597de8423179773d910d9a7b3d945cb2c3b7e1c2/analysis/
44 http://www.cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2012-0158
45 http://technet.microsoft.com/en-us/security/bulletin/ms12-027
46 https://web.archive.org/web/20130723051052/http://ariave.com/tech.htm
47 On 20 December 2013, Belgium?s time zone was 6 hours ahead of Northern Virginia?s.
48 The article quotes the former head of Ethiopia?s Amhara region (Ayalew Gobeze) as denying that he was demoted or fired for failing to sign a border demarcation agreement between Sudan and Ethiopia. Ayalew is quoted as saying that members of the Ethiopian diaspora concocted the story, and refers to them as ?taxi drivers? and ?jobless?.
Ronald Deibert
Director, the Citizen Lab
and the Canada Centre for Global Security Studies
Munk School of Global Affairs
University of Toronto
(416) 946-8916
PGP: http://deibert.citizenlab.org/pubkey.txt
http://deibert.citizenlab.org/
twitter.com/citizenlab
r.deibert at utoronto.ca
-------------- next part --------------
An HTML attachment was scrubbed...
URL: <http://mailman.stanford.edu/pipermail/liberationtech/attachments/20140212/5823463d/attachment-0001.html>